Archive for January, 2011
Password Cracking
Posted by Spoonman1091 in Uncategorized on January 22, 2011
In the last post, I mentioned that it may take quite a long time to crack an NT hash, but there are many methods for cracking passwords. I will walk you through one simple method. There is an excellent guide posted on Offsec that describes the many other various methods available.
One of the fastest methods I know to crack passwords is by using Rainbow Tables. Instead of running through all of the combinations to crack the hash in real-time, the tables are generated before-hand. The main limitations of Rainbow Tables are the size and time it takes to generate them, although there are many pre-computed tables online that are available to download. There are also a number of different versions of tables, so you need to know before hand what type of hash you are trying to crack (LM, NTLM, MD5, SHA1, etc.).
If you remember from the “Pass The Hash” post, we obtained the hash for the local Administrator account:
Administrator:500:NO PASSWORD*********************:8846F7EAEE8FB117AD06BDD830B7586C:::
We know that the hash is from a windows machine, so the hash is going to be either LM or NTLM. Since the first byte of the hash is not available, we know that it is an NTLM hash. So, we know we are going to need an NTLM table to crack this password.
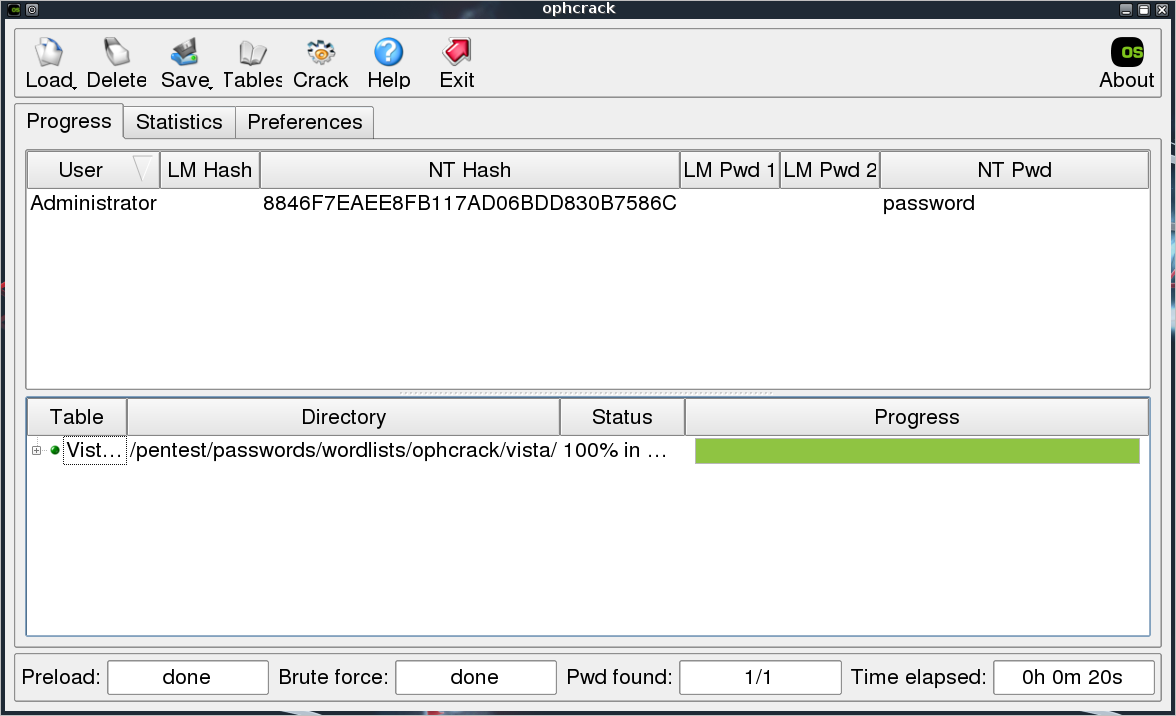
Ophcrack is a very simple tool created by the original developers of Rainbow Tables. It uses a custom version of the tables, so it can only be used with the tables available on the site. There are two LiveCD’s available for download, one for LM hashes (XP LiveCD) and one for NTLM hashes (Vista LiveCD). Since I like to do everything from BackTrack and Ophcrack is already available in the distribution, all we have to do is download the tables. So, we just download the “Vista Free” table, insert our hash, and click “Crack”.
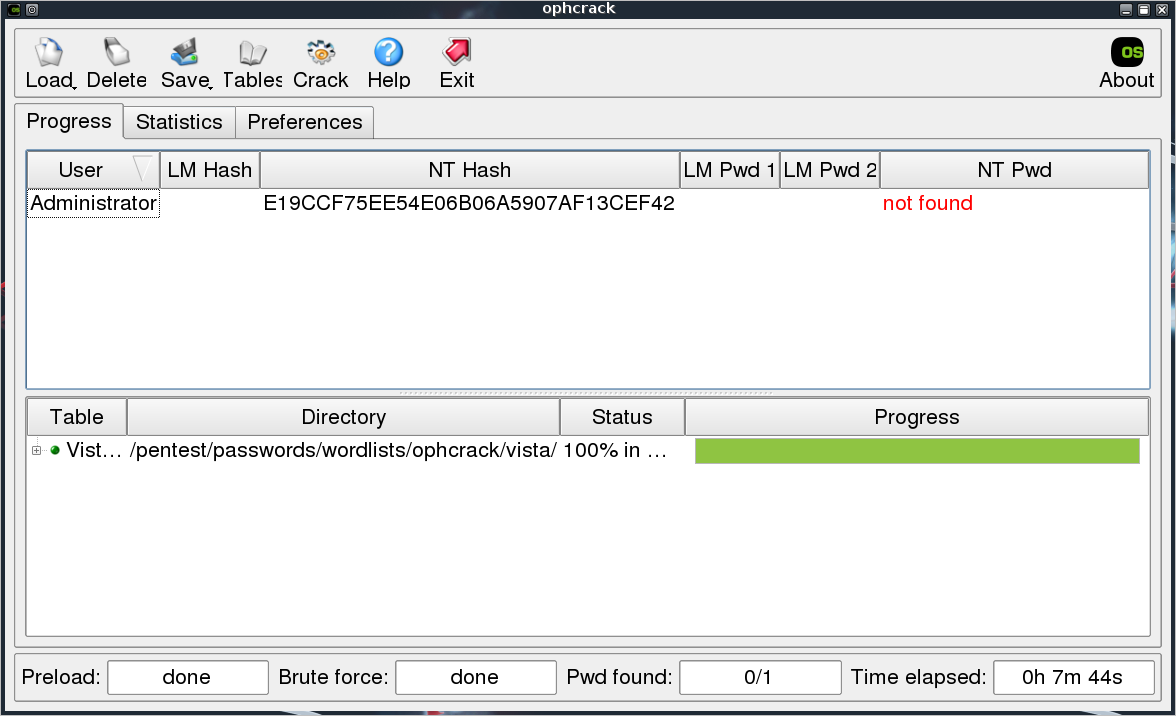
Twenty seconds later, we have the password “password”. That was too easy. This particular table is based on a dictionary, so it’s not going to crack anything too complicated. Let’s try the hash for “P@ssw0rd”. It contains an uppercase, lowercase, digit, and special character, but still isn’t a very secure password.
Password not found :-( So, this table isn’t exactly fool proof, but it is a quick and dirty way to catch some low hanging fruit.
Happy Cracking!